20
Jan
MailStore 9.1 Brings Email Archiving for Google Apps
 We've just made the latest version of MailStore live on our site and if you, or perhaps your customers, are users of Google Apps, it's one I highly recommend you download.
The ability to archive Google mail isn't completely new to MailStore, however in previous versions, each mailbox would need to be archived individually, requiring a separate archiving 'job' and manual entry (and ongoing maintenance) of username and password credentials.
In version 9.1, the German developer have now made the whole process a breeze.
We've just made the latest version of MailStore live on our site and if you, or perhaps your customers, are users of Google Apps, it's one I highly recommend you download.
The ability to archive Google mail isn't completely new to MailStore, however in previous versions, each mailbox would need to be archived individually, requiring a separate archiving 'job' and manual entry (and ongoing maintenance) of username and password credentials.
In version 9.1, the German developer have now made the whole process a breeze.


 You may have picked up in the IT press recently that we're starting to see an industry-wide movement to a new, and importantly more secure, standard of SSL certificate.
Alt-N Technologies, developer of the Exchange alternative
You may have picked up in the IT press recently that we're starting to see an industry-wide movement to a new, and importantly more secure, standard of SSL certificate.
Alt-N Technologies, developer of the Exchange alternative  We recently needed to migrate our own internal MDaemon and SecurityGateway server to a new location. Luckily we often do this for customers and we have guides specifically written to help with this process.
We recently needed to migrate our own internal MDaemon and SecurityGateway server to a new location. Luckily we often do this for customers and we have guides specifically written to help with this process.
 This year in particular, I've seen an increasing number of users' email account credentials become compromised, which has allowed spammers free reign to use their mail server to send spam out to the Internet.
The usual result is an overflowing outbound mail queue, thousands of bounce messages coming in and your server's IP address being blacklisted.
The first thing to note is that if your company has an email server, you should assume that spammers will always be trying to hijack users' accounts by guessing their passwords.
In this post I will run through a few simple pro-active settings checks that can reduce the chances of this happening and - in the unfortunate event that it does happen - can limit the resulting negative effects.
This year in particular, I've seen an increasing number of users' email account credentials become compromised, which has allowed spammers free reign to use their mail server to send spam out to the Internet.
The usual result is an overflowing outbound mail queue, thousands of bounce messages coming in and your server's IP address being blacklisted.
The first thing to note is that if your company has an email server, you should assume that spammers will always be trying to hijack users' accounts by guessing their passwords.
In this post I will run through a few simple pro-active settings checks that can reduce the chances of this happening and - in the unfortunate event that it does happen - can limit the resulting negative effects.
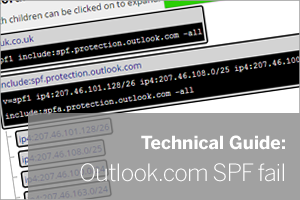 Over the last 24 hours we have seen a few instances where valid email from Outlook.com servers has been rejected by our customers MDaemon and SecurityGateway servers due to SPF record checks.
The emails getting rejected do appear to be valid messages but have been arriving from an IP address not included in the sending servers SPF records. The common factor here is that all the sending domains are using outlook.com services.
Over the last 24 hours we have seen a few instances where valid email from Outlook.com servers has been rejected by our customers MDaemon and SecurityGateway servers due to SPF record checks.
The emails getting rejected do appear to be valid messages but have been arriving from an IP address not included in the sending servers SPF records. The common factor here is that all the sending domains are using outlook.com services.
 If you're using Office 365, or one of the many hosted Exchange variants available today, you may be aware that MailStore has long been able to give you a complete and automatically synchronised off-site copy of your mail.
I've always been happy recommending it as a solution,
If you're using Office 365, or one of the many hosted Exchange variants available today, you may be aware that MailStore has long been able to give you a complete and automatically synchronised off-site copy of your mail.
I've always been happy recommending it as a solution,  If you've recently made the move to MailStore version 9, it's entirely possible you'll be sat there wondering why on earth all of those archiving jobs you had set up can't be modified any more.
If you've recently made the move to MailStore version 9, it's entirely possible you'll be sat there wondering why on earth all of those archiving jobs you had set up can't be modified any more.
 Today's nugget of MDaemon wisdom comes from conversations I've had with a small number of customers reporting they're unable to send outbound email to specific recipients.
Upon closer inspection of the error in the SMTP (OUT) log, there's a message reading "SSL negotiation failed".
Today's nugget of MDaemon wisdom comes from conversations I've had with a small number of customers reporting they're unable to send outbound email to specific recipients.
Upon closer inspection of the error in the SMTP (OUT) log, there's a message reading "SSL negotiation failed".
 Configuring any Web service to work over HTTP using SSL is a good idea.
We certainly recommend it for BackupAssist's Multi-site Manager (BAMM) and in this post I'll show you how to create an SSL certificate you can then bind this kind of service to.
Configuring any Web service to work over HTTP using SSL is a good idea.
We certainly recommend it for BackupAssist's Multi-site Manager (BAMM) and in this post I'll show you how to create an SSL certificate you can then bind this kind of service to.
 A new SSL vulnerability is doing the rounds this morning, known as POODLE, or Padding Oracle On Downgraded Legacy Encryption.
POODLE is a newly disclosed vulnerability in the legacy SSL 3.0 protocol that could be exposing users of newer Transport Layer Security (TLS) encryption protocols to risk.
If exploited, the POODLE flaw could potentially enable an attacker to access and read encrypted communications.
A new SSL vulnerability is doing the rounds this morning, known as POODLE, or Padding Oracle On Downgraded Legacy Encryption.
POODLE is a newly disclosed vulnerability in the legacy SSL 3.0 protocol that could be exposing users of newer Transport Layer Security (TLS) encryption protocols to risk.
If exploited, the POODLE flaw could potentially enable an attacker to access and read encrypted communications.