19 Dec Limit the Chance of Your MDaemon Accounts Being Hijacked and Abused by Spammers
 This year in particular, I’ve seen an increasing number of users’ email account credentials become compromised, which has allowed spammers free reign to use their mail server to send spam out to the Internet.
This year in particular, I’ve seen an increasing number of users’ email account credentials become compromised, which has allowed spammers free reign to use their mail server to send spam out to the Internet.
The usual result is an overflowing outbound mail queue, thousands of bounce messages coming in and your server’s IP address being blacklisted.
The first thing to note is that if your company has an email server, you should assume that spammers will always be trying to hijack users’ accounts by guessing their passwords.
In this post I will run through a few simple pro-active settings checks that can reduce the chances of this happening and – in the unfortunate event that it does happen – can limit the resulting negative effects.
1) Passwords
Make sure that all your accounts have strong passwords that cannot be guessed by spammers and that, ideally, are not used elsewhere.
Don’t use the same password across multiple accounts and definitely avoid setting the password to match the account username – both situations are asking for trouble!
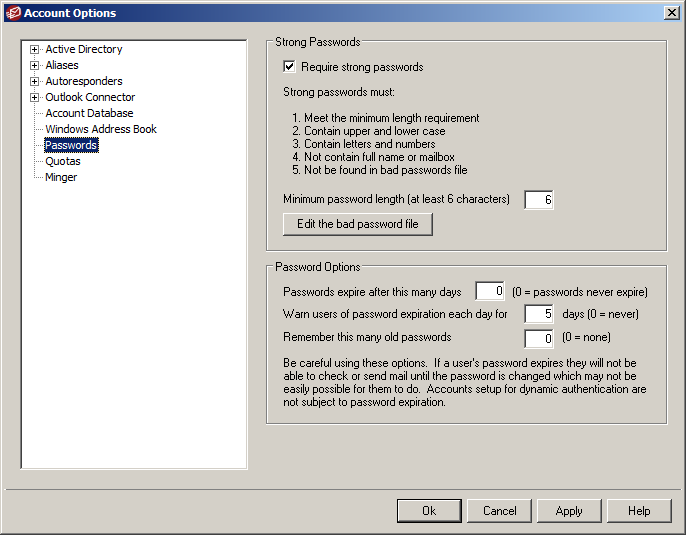
Configure your server to require strong passwords and update the ‘Bad password file’ to stop users configuring passwords that are insecure. The default and recommended settings are shown below and can be found in the MDaemon under Accounts -> Account Options -> Passwords:-
Check the settings shown below on your server. The ones shown are our recommended defaults and should only differ in very specific situations. All the following settings are found in the MDaemon GUI under Security -> Security Settings:-
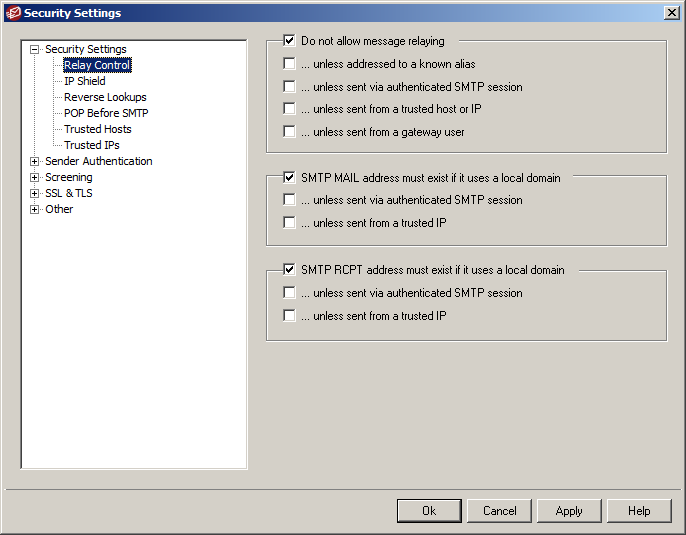
2) Relay Control
Relaying is where email is neither to or from a local user. It’s very rare that you ever want to allow your server to relay mail. These settings also ensure that any email sent or received is only sent from addresses which exist on the server.
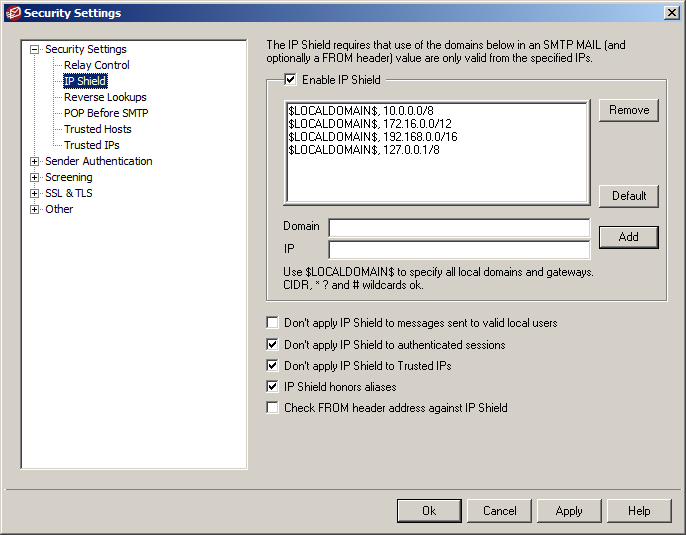
3) IP Shielding
The IP shield enforces the requirement that email being sent from local addresses must originate from specified IP ranges (the defaults include all the standard IP ranges reserved for internal use). Authenticated users bypass this requirement (needed if the user is sending email from outside the local network).
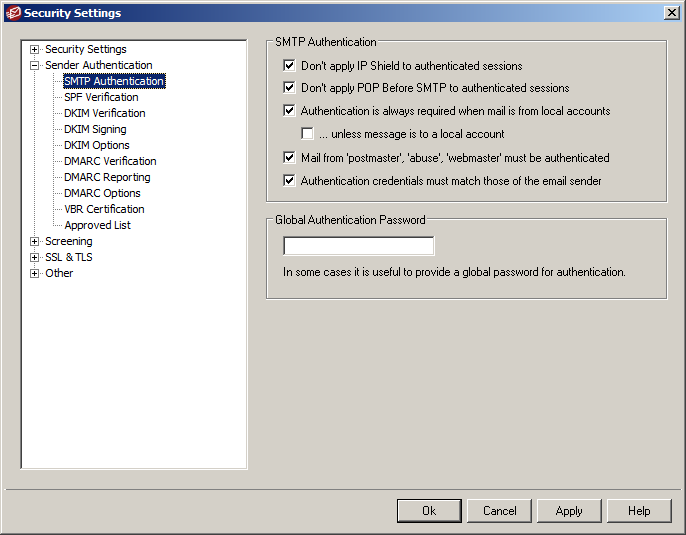
4) SMTP Authentication
Enforcing SMTP Authentication as much as possible is a good thing in all cases. It’s only in very rare situations that you would want to relax these requirements.
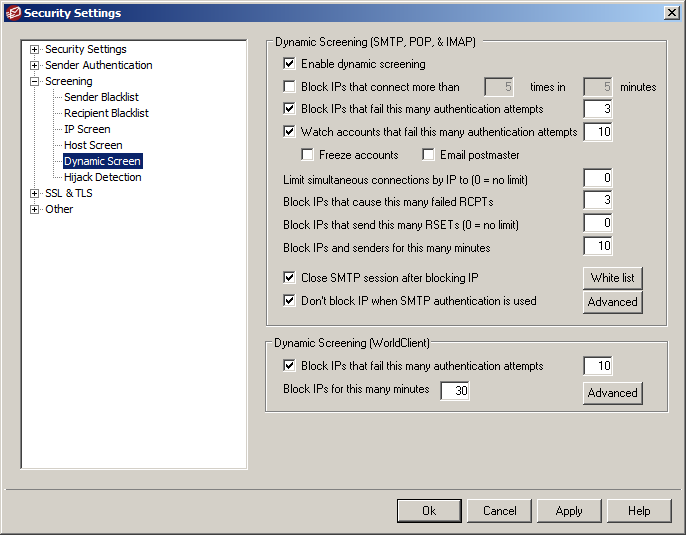
5) Dynamic Screen
Dynamic screening monitors for suspicious activity and dynamically blocks connecting IP addresses for a period of time which is very effective in limiting spammers’ ability to hijack your users’ accounts.
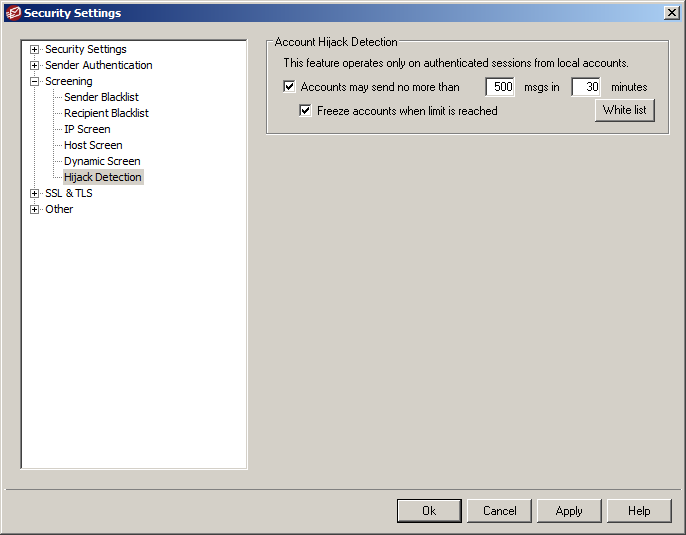
6) Hijack Detection
This feature simply freezes any accounts which start sending a high volume of email in a set period of time and is useful in limiting problems caused by accounts which have already become compromised. Obviously, if you do have accounts which legitimately send large volumes of email, then you will want to whitelist them.
Hope you found that useful – as always, if you have any questions or comments, please feel free to leave them below.
Useful links:
– More information and a free 30 day trial of MDaemon Messaging Server

