20 Aug MDaemon 13 beta preview: Part 3 – Detect and stop hijacked MDaemon accounts
 One of the more common customers support calls i get relates to MDaemon suddenly sending vast amounts of spam email. This floods the outbound Internet connection and everything crawls to a halt.
One of the more common customers support calls i get relates to MDaemon suddenly sending vast amounts of spam email. This floods the outbound Internet connection and everything crawls to a halt.
Secondary to this the server’s public IP address can get listed on various external SMTP blacklists which the customer then has to request removal from.
When you’re running a business this clearly isn’t a good situation to be in and the customers I speak to are understandably want to quickly understand what has gone wrong and what can be done to stop it happening in the future.
99% of the time these problems boil down to one or more of the MDaemon user accounts getting hijacked. The password is guessed and then used to authenticate the SMTP session with MDaemon, therefore bypassing a majority of the security features, allowing an external spammer to send huge volumes of SPAM email.
As you may have already gathered from one of my earlier posts I always recommend you use strong passwords on all of your MDaemon user accounts to minimise the chance they can be compromised in this way. However, there are still many installations out there with easy to guess passwords or passwords that are shared across a variety of external systems.
To help combat this issue and minimise the impact of a hijacked MDaemon account, a new feature has been added in version 13 to detect large volumes of email being sent in a short space of time from a specific account, and block it from sending any more until further manual investigation.
By stepping in and blocking the account before too many SPAM messages get out, the likelihood of getting blacklisted is lowered and the password can be changed on the compromised account to get it up and running quickly.
The new feature In MDaemon is under the Dynamic Screening security section.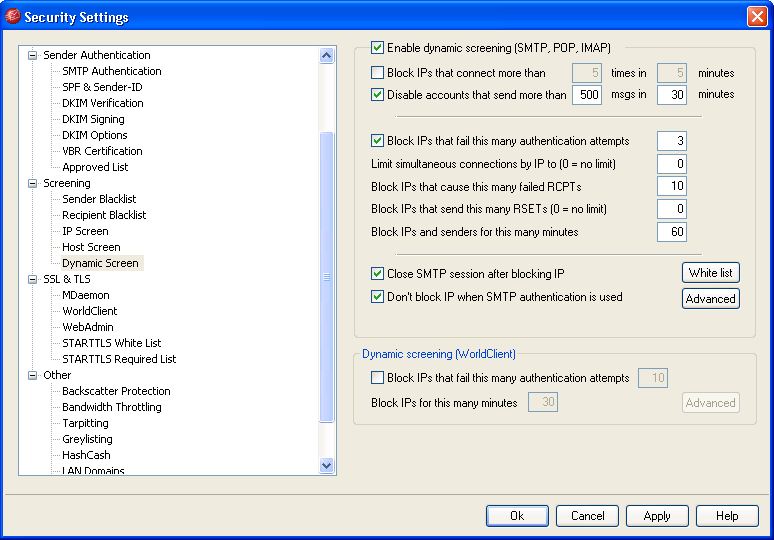
This feature restricts an account to only send x messages in x minutes. The defaults are set at 500 messages in 30 minutes, which should be about right for the average MDaemon user but they can be customised if this is too restrictive.
When this limit is triggered the account gets de-activated and an alert email is sent to the postmaster account so they’re able to decide whether there’s an issue.
If the alert is a false positive (maybe the user is sending out a very large volume of mail) then the postmaster can simply reply to the alert email to re-activate the account.
I think it’s definitely worth having this switched on as the chance of incorrectly detecting a hijacked account is low and even if one is disabled it’s quick and easy to re-enable it. Of course this should not stop you using strong passwords for all your accounts!

