31 Aug Can Ransomware Infect the Backups of your MSP Customers?
Ransomware is right up there as one of the worst types of malware your clients are likely to come across.
Not only is there the risk of being locked out of computer systems or important databases, but there’s the additional risk of public backlash and damages to reputation.

As you’ll have no doubt seen in the press – if the breach is large enough, ransomware attacks can easily become high-profile media events and the ransom demands can be incredibly tricky to manage.
If they do pay the ransom for their data, not only is it an admission of defeat, but it can also be a significant financial hit.
What’s more, there’s really no guarantee they’ll gain access to their systems again.
Once the scammers have their money, there isn’t anything but goodwill compelling them to return what was already taken.
The ideal outcome for a situation like this is obviously one where you don’t pay at all, but that means holding some or all of the cards ahead of time. The way most organisations do that is to safeguard data and prevent these attacks through one, extremely efficient method: backups.
Backups are at the heart of every client’s contingency plan for data loss or lockout.
The only question is, are backup systems really that safe? Or are they another risk waiting to be exploited by ransomware?
Can Backups be Infected by Ransomware?
Sadly, the answer here is yes. Backups can be infected by ransomware.
But let’s not dwell on that because the good news is that this infection doesn’t transfer by magic.
If your customer’s backup is a secured external hard drive tucked away somewhere, left unplugged from anything, then of course this data will be fine. For the moment, at least. The issues arise when clients attempt to access their backups.
A typical ransomware to backup situation tends to play out like this:
- A client realises their files have been encrypted by ransomware. This often happens when they can no longer access computers or files, but the realisation can sometimes occur later, when they receive the actual email outlining the list of demands or terms of the ransom.
- At this point, instincts kick in. The client isolates the infected systems, reboots the computer into a recovery environment, and runs a malware removal tool.
- After some time, the computer passes all the checks and the ransomware appears to have been purged. Often, these safeguarding steps can have the client feel pretty confident that they have isolated the problem and prevented a catastrophe.
- After that, however, it’s time to dust off that old external drive, plug it into the computer, and retrieve the critical files that were lost.
Good as new, right? Well, maybe not.
Attaching your backup to a previously compromised system is an incredibly common mistake made after a ransomware attack, and sometimes an extremely costly one.
It only takes a couple seconds for the ransomware to reactivate; encrypting your backups and putting you right back where you started, but this time probably without a plan B.
Always Air Gap Your Backups

There are several ways ransomware can gain access to your backups.
In the previous instance, a lot was actually done correctly to prevent contamination, but some critical errors were made that compromised a solid start.
To begin with, having an external, secured backup is the foundation of any good contingency plan. Equally important, however, is ensuring that the backup is “air-gapped.”
It is best practice to always have a backup that is disconnected and offline, to ensure it is completely isolated from external systems that might be used to access it.
Where the client in the example failed, was by trusting the malware removal tool, and thus violating another key step to take in these instances: isolation.
Isolating the infected system from other systems is key, but by trusting the malware removal software to do its job completely instead of having the 99% mentality, the client made the mistake of connecting the backup to the computer automatically, thus violating the isolation of both.
Failure to create an “air-gapped” backup, or violating the isolation of infected systems is one of the key ways ransomware gains access to backups. In the current age of ever-increasing interconnectivity, programs like OneDrive or Google Drive are often relied on as easy-to-use backup systems, particularly for group work.
The issue here is that these systems are inherently difficult to isolate and impossible to air gap. All it takes is one user with access to suffer a ransomware infection, and the whole system is then potentially compromised.
How Common are Ransomware Attacks?
This may all sound pretty concerning, but it’s important to analyse the likelihood of a ransomware attack based on your business and access routes.
Often, the necessity of security precautions are judged not on the potential damage of malware attacks, but on the likelihood.
In recent years, ransomware has become increasingly common, with some reports for 2020 stating 304 million instances occurred.
With the rising necessity of remote work and its supporting software in 2021, that number is expected to go up even more. This increase is accompanied by a rise in the high-profile nature of attacks, with larger organisations being targeted for much larger sums.
Famously, the attack on Colonial Pipeline resulted in them paying a $4.4 million (£3.1 million) ransom. A controversial decision was made in the interest of keeping vital infrastructure running.
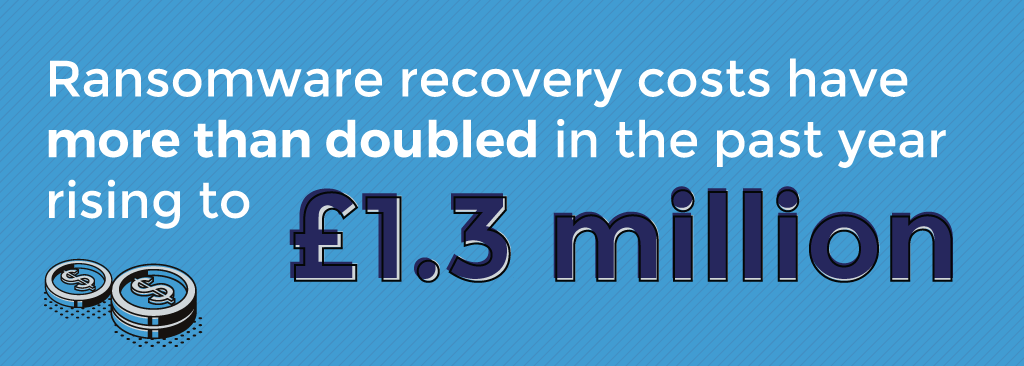
When you consider that the average ransom paid being £124,308 in 2021, you can see how ransomware recovery costs including the ransom have more than doubled in the past year, rising from £555,221 in 2020 to £1.3 million in 2021.
And these attacks aren’t just limited to single companies. As systems have grown more integrated, so too have companies. The July hack of the information technology firm Kaseya this year may have resulted in between 800 to 1,500 connected businesses being compromised.
How Can Backup Infection Be Prevented?
We’ve covered some of the preventative measures that can be taken to secure backups, and the need to react properly when a ransomware attack has happened—but there are other options available for active defence.
BackupAssist, for example, is a server backup software for growing businesses that need reliable, automated protection, without great complexity or expense. Launched in 2017, it benefits from two innovations that help to counteract ransomware and other malware attacks.
The first innovation is the shield.
Designed to protect your backup from unauthorised access and prevent corruption, the shield is your first line of defense against malicious programs that might seek out your data.
The second innovation is early detection.
This ensures that only the files you mean to back up, are backed up.
Ransomware can sometimes corrupt overlooked files, using them as a way to infiltrate your backup and infect it from the insides. Through early detection, dangerous files are screened and prevented from going where they shouldn’t.
By combining the shield and early detection, BackupAssist ensures you can back up all of the data that’s important to your business, to almost any destination you deem safe. With that in mind, reliable server backup doesn’t have to be complicated. Or even expensive.
BackupAssist provides all of the tools you need to protect both physical and virtualised servers, without draining your IT budget in the process.
Want to learn more about BackupAssist and CryptoSafeGuard?
- More information, pricing and a free 30-day trial of BackupAssist
- Help guides for CryptoSafeGuard (vendor website)

