05 Jun Protecting Against Ransomware – An MDaemon Admin’s Guide
Unless you’ve somehow managed to avoid both the news headlines and the barrage of content from IT security vendors that followed, you’ll no doubt be aware that a couple of weeks ago, there was a particularly severe ransomware attack that affected over 100,000 businesses around the globe, including the NHS.
The latest evidence indicates that the recent ‘WannaCry’ attack originated via an exploit tool created by the NSA, however it’s more common they originate via ‘phishing’ emails, the technique of tricking recipients into clicking a malicious link or opening an attachment, often appearing to be from a colleague or relative.
So with this in mind, now seems like a great time to give you a refresher on the features at your disposal as an MDaemon administrator to help prevent the type of phishing attack that can lead to a ransomware infection, along with some additional tips on best practice.
(Almost all of the security tools for MDaemon are in the SecurityPlus add-on so for the purpose of this post, I’ll be assuming you’ve got that installed.)
Origin and reputation
Even before MDaemon takes receipt of an email, it performs a number of checks using the information in the headers of messages to establish the likelihood it’s come from a trusted source.
Checking of DNS blacklists
A simple check against a blacklist is often all it takes to spot an attack.
MDaemon takes the sender’s IP and references it against a trusted DNS blacklist source. Repeated offenders very quickly end up on these lists so it’s a good first step to filter out obvious bad senders.
Banning of senders without Reverse DNS (RDNS) configured
Like the blacklist feature, a reverse DNS check also uses the sender IP, but this time it’s cross-referenced with the information held at the ISP for that domain, in order to check it exists and is genuine.
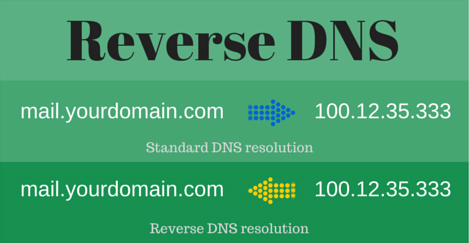
This is particularly effective as it helps identify mail sessions originating from ‘zombified’ workstations being used to spam, because it’s very unlikely they’ll have a valid record setup, unlike a legitimate business server.
Since both Google and Microsoft now require you have a valid RDNS entry in your domain if you want to send to their mail platforms, we’ve reached a point where we’re now also comfortable recommending you take the step of denying senders without a valid record too.
Further reading:
Using Reverse Lookups To Prevent Spam (blog post)
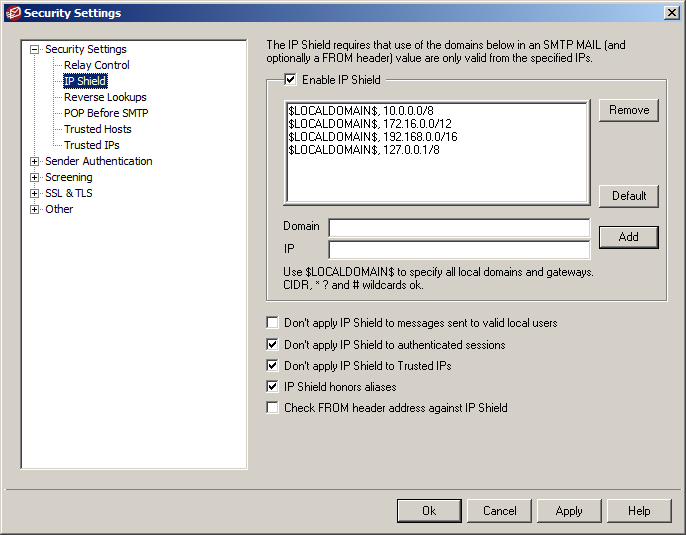
IP shielding
MDaemon’s ‘IP Shielding’ feature prevents spoofed emails arriving that claim to be from other staff members (ie. coming from a local email address), but that actually originate from an external IP address that’s not trusted.
We highly recommend you configure MDaemon to check both the ‘return-path’ email address and the one in the ‘FROM’ header as shown to help detect additional potential spoofing attacks.
Further reading:
How to set up IP shielding (knowledgebase article)
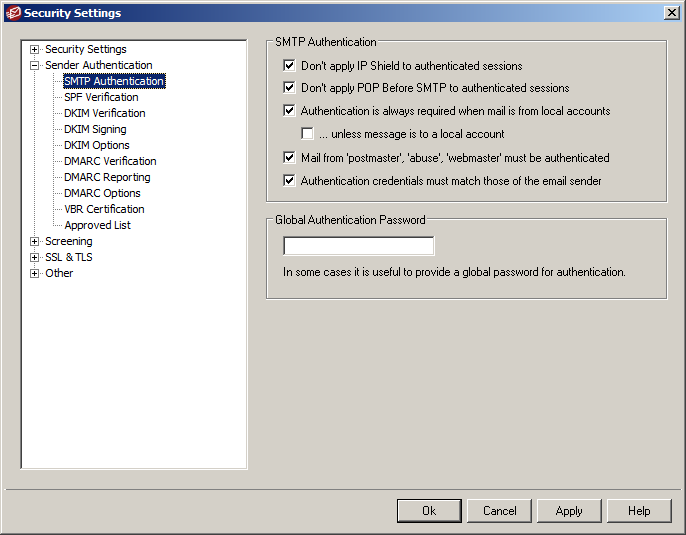
Enforcing SMTP authentication
If you don’t already, we highly recommend you enforce SMTP authentication as it ensures everyone, and everything sending via your mail server, are required to log in with a username and password (secure preferably!).
It’s not always possible if you have devices in your network without the option to authenticate, but if you can implement it then you should, as this will significantly reduce the chance your users will receive a spoofed email posing as another member of staff from your company.
Further reading:
How to configure SMTP authentication (YouTube)
Check reputation using SPF and DKIM
Also working to keep unwanted mail away are two reputation checking features, Sender Policy Framework records and DKIM (DomainKeys Identified Mail).
With both of these configured, when an email arrives for one of your users claiming to be from your domain, your server will check it originated from a reputable source, discarding those claiming to be from external domains that have been spoofed.
Further reading:
All about Sender Policy Framework Records (blog post)
Configuring DKIM in MDaemon (YouTube)
Zero-hour
Cyren ‘Outbreak Protection’
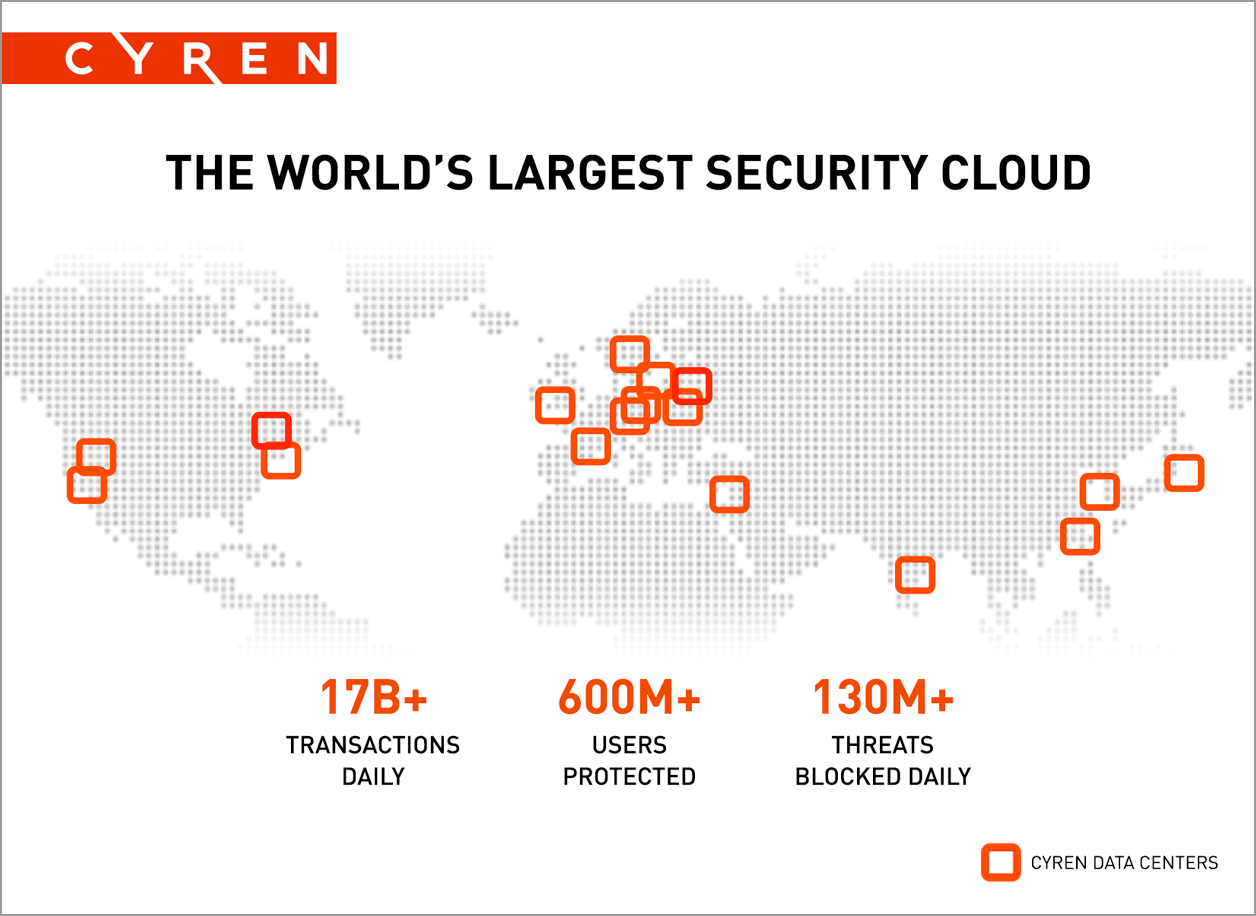
MDaemon is equipped with Outbreak Protection from Cyren, the vendor who provide the security technology for cloud platforms such as Microsoft, Amazon and Checkpoint.
Outbreak Protection is fully automated and creates a hash of every incoming email, including the links and attachments, referencing it against Cyren’s GlobalView™ Security Cloud which is analysing billions of globally collected emails every day from the largest threat analysis platform of its type in the world.
This feature will be on be default in MDaemon and there’s no real maintenance to do for administrators, however, it’s perhaps the most effective tool of them all in the MDaemon armoury. We’re extremely happy with the performance we see from Cyren in those early moments of malware outbreaks and also later on as we start to see the variants emerging.
Further reading:
Cyren Zero-Hour Protection (Cyren.com)
Message Content Analysis
Let’s just say an unwanted message does make it past the checks we’ve talked about above, it still hasn’t actually been delivered to users, it’s just been accepted by MDaemon for further analysis.
Twin virus engines
Cyber-security can be compared to a high-tech game of cat and mouse. No security vendor can genuinely claim they’re able to stop every new threat, simply because the techniques being used evolve so quickly. Instead, they focus their considerable resources on minimising the window of time an attack is active for.
By combining Cyren’s Outbreak Protection and two virus engines in the form of global security giant Kaspersky Labs and ClamAV, the open source engine used by millions around the world, that window of time is kept to an absolute minimum.
These engines analyse all message content in order to quickly establish whether it’s a virus, DDoS attack, malware, ransomware, phishing attempt or worm. Threats are then quarantined, normally destroyed and delivery refused.
Once a Message Reaches the Mailbox
OK, so the attackers have come up with something pretty special this time and it’s managed to make it past MDaemon’s many layers of security – is there anything left that you can do as the administrator at this point?
Enable ‘FROM’ header modification
Email clients like Outlook usually display only the sender’s name, and not the actual sending email address, which means it’s simple to disguise an email as being legitimate when the address behind the name is actually that of an attacker.
MDaemon now offers the option of taking that originating address and making it the first thing you’ll see in Outlook rather than the person’s name.
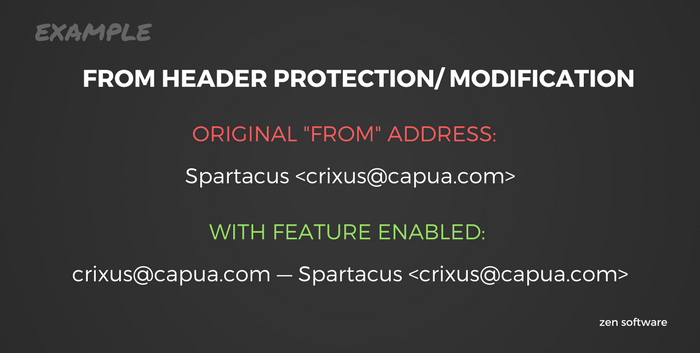
It’s not for everyone as it does mean the ‘friendly’ name is less visible, but for the ultra paranoid, it is an effective way of spotting spoofed email so something we recommend you give a trial run.
Don’t click on that! User education around phishing emails
It’s estimated that 36% of UK office workers “could not confidently define a phishing attack” and 76% don’t know what ransomware is, according to a 2016 study by ISACA.
Cyber-attacks rely heavily on the bad practices we pick up as email users. While they are unfortunately more common than they should be, there’s no reason you can’t significantly diminish the risks by educating users on the signs to look fo, such as…
Further reading:
Protecting Your Business from Spear Phishing (blog post)
Last chance saloon
I hope I don’t need to remind you of the importance of a reliable backup strategy for your business, but I will anyway. In the fight against ransomware, it’s absolutely critical. It’s also important that you incorporate an ‘air-gap’.
This somewhat mysterious term simply means that there is no wired (or wireless) connection between device A and device B, so you’ve established a gap between a potential hacker and your data.
Basically, if you’re currently relying only on backing up to an extra hard disk or even a network share, you should really think about introducing offline media of some kind.
BackupAssist is the product we recommend as it supports rotatable media such as USB drives as well as backup direct to Amazon and Azure, but there are lots of alternatives available too.
Further reading:
What is an air-gap and should you do it? (BackupAssist blog post)
A technical overview of BackupAssist (YouTube)
In Summary
The not so good news I’m afraid is that cyber attacks are a problem that isn’t going away and no security vendor can legitimately promise you total immunity.
The good news is that if you correctly configure the tools available to you in MDaemon, educate your users and put in place a fail-safe of a proper backup strategy, you have a numerous layers of highly effective protection, and a plan B just for extra peace of mind.
Further information:
Protecting Against Ransomware – An MDaemon Admin’s Guide (Infographic)
Protecting Against Ransomware – An MDaemon Admin’s Guide (YouTube video)