17 Nov Protecting Your Business from ‘Spear Phishing’
 While it’ll probably never be 100% effective, the level of email security we have available to us today is less expensive and more effective than it’s ever been.
While it’ll probably never be 100% effective, the level of email security we have available to us today is less expensive and more effective than it’s ever been.
This may go some way to accounting for the recent rise, and added sophistication in phishing attacks as criminals choose to target the new weakest link, now located between the chair and keyboard.
Introducing ‘spear phishing’
‘Spear phishing’ is a particularly effective way of tricking us into handing over various details including card info, financial records and more using social engineering.
Attackers gather information from social media, email account monitoring and other sources to help them craft emails that seem to be from people and companies we know and deal with on a regular basis.
Spear phishers take advantage of familiarity – because the email seems to come from someone you know, they’re relying on the fact you’ll be less vigilant. And if an instruction arrives marked as urgent, that you may just act before you think.
How it works
In the past the main threats you were likely to see were nearly always from external sources and fairly obvious if you had a rough idea of the things to look out for. Now however, it’s possible they’ll come from the company director asking you to pay an invoice and there’ll be very little clue.
It’s also possible that the payment references a valid customer and even an amount for a valid invoice but yet the account details are false.
Business practices to avoid
These social engineering attacks rely heavily on the bad practices within companies that are unfortunately more common than they should be.
Some of the key things to avoid are…
- Relying on email as the only mechanism to authorise a payment – qualify payment requests with a call or a fresh email to the sender (do not just reply!).
- Sending bank details in an email – always check invoice details with those held on file or via a phone call or text message where possible.
- Trusting email as secure – remember that email is insecure by its nature. Think of it as such and always verify authenticity.
Tell-tale signs to look for
The good news is that phishing attacks can be prevented, defence is primarily about being vigilant and knowing the signs to look for.
If you have suspicions, another good check is to view the message header as it’s likely the attacker will have change the ‘From’ name.
- Start Outlook.
- Double-click the message for which you want to view full internet headers.
- Click Options (2007) or Tags (2010/2013). / The Message Options dialogue box is displayed.
Configuring MDaemon to protect against phishing attacks
Even though this type of attack relies on social engineering of the recipient, if you’re a user of MDaemon Messaging Server, there are some quick and easy tweaks you can make to give you the best possible defence.
1) Stop spoofed email from internal addresses
A quick fix is to stop spoofed email arriving that claims to be from internal email addresses.
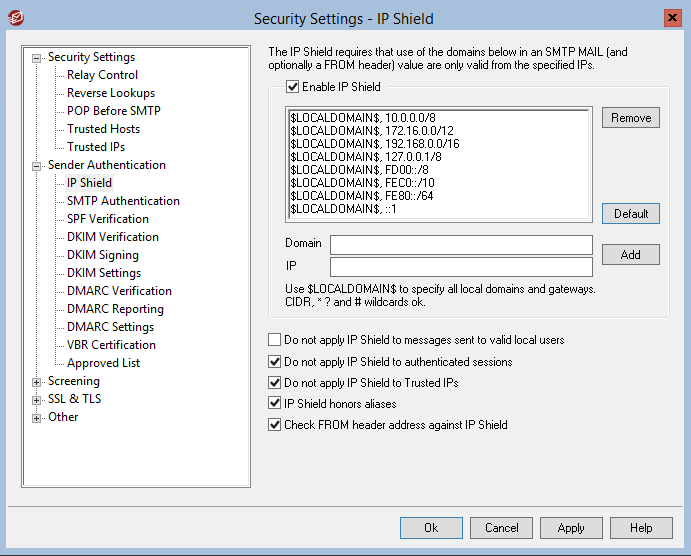
This can be configured under Security > IP Shield by ticking the option ‘Check FROM header against IP Shield’
2) Reputation features – SPF and DKIM
In addition to this you should also consider protecting your own company domain using MDaemon’s reputation features which include Sender Policy Framework records and DKIM.
Once configured, when any email server (including your own) receives an email claiming to be from your domain, the receiving server checks if it came from a reputable source, quickly discarding spoofed emails from untrusted sources.
These features protect your domain publicly and a receiving server can be sure that any email it received claiming to come from your own domain is actually coming from a valid server you manage.
Be vigilant folks
If you’re being asked for a payment, for your personal details or perhaps some bank account information, spend just a moment to cast your eye over the sending domain and the link.
Just a second look for incorrect characters or links that don’t point where you’re expecting could save you an inordinate amount of time, inconvenience and cost.
I hope that helps – as always, comments and questions welcome in the usual place (down there :))

