20 Nov Fake Invoice Spam – Five Defensive Tweaks For Your MDaemon Email Server
Ah, the good old days of Windows ’98.
That period will, of course, stick in your mind for ‘Bootie Call’ by All Saints topping the charts, and the release of the undisputed king of phones, the Nokia 5110.
They were, however, magical times for another reason.
Our businesses weren’t under permanent attack.
In 1998, the sum total of the average small company’s cybercrime ‘strategy’ was a copy of Dr Solomon’s, and making sure your password Post-it went in your drawer at the end of the day.
Gone phishing
Roll forward to today and Europol’s former head of cybercrime is of the opinion that cybercrime is the biggest threat to all organisations around the globe.
Hackers are working tirelessly to find new techniques for making the lives of business owners more difficult, and the flavour of recent month has been the use of phishing emails with fake invoices.
These emails, loaded with trojan malware, are designed to dupe you into opening what you would assume is an office document like any other.
Instead, they install a malicious payload on your machine that will do a variety of delightful things, ranging from pinching your credentials and logging your keystrokes to encrypting your files and holding them ransom.
How can MDaemon help?
As an MDaemon user, you are in a good place.
You are already well equipped with a great armoury of security tools. However, it is a game of cat and mouse that moves at a frightening pace, so it’s important not to become complacent.
The latest release of MDaemon, like many before it, includes a new feature to bolster defences (see tip 5 below), so the quickest win is to make sure you’re always on the most recent update.
Beyond that, I’ve listed some specific adjustments to settings and other suggestions you should consider to ensure you’re doing everything you can to deal with this particularly nasty threat.
1) Check more frequently for updates
Ensure that both Setup -> Event Scheduling -> Antivirus -> Scheduling and Security -> ClamAV Plugin are set to perform very regular antivirus definition updates (we’d recommend every hour).
This helps ensure that the latest virus definitions from Cyren and Clam Antivirus (the antivirus engines MDaemon is using) are always available when it’s scanning email.
Note: Given the frequency of the updates following this modification you may choose to enable Security -> Antivirus -> Recipients -> ‘Only send antivirus update notification on failure’ to reduce the number of antivirus definition update emails you receive.
2) Report anything that slips through the net
If a virus is missed, you can upload the attachment to https://www.virustotal.com/ to see if Cyren and Clam Antivirus have definitions for it yet.
If they don’t, you can pass them back to these engines to as false negatives via https://kb.cyren.com/av-support/?/Tickets/Submit/RenderForm/7 and https://www.clamav.net/reports/fp as applicable.
3) Start checking old messages
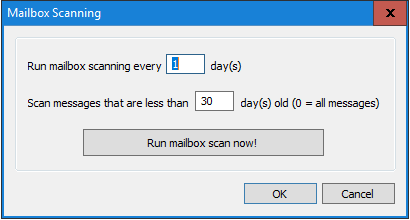
If a virus definition that would catch these emails isn’t available at the point an email is accepted it may be later so you can catch those emails that might have been missed in the mailbox directly by configuring Mailbox Scanning in Security -> Antivirus…
You can configure this to run every night if you wish and then act on email within a defined period to help limit any potentially associated load it creates…
The way this process works is as follows…
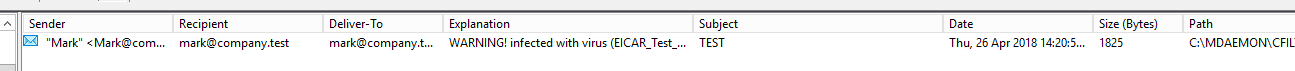
The mailbox scan logs to a \MDaemon\Logs\SPScanCT-YYYYMMDD.log file and a detection looks like this (click images to expand)….
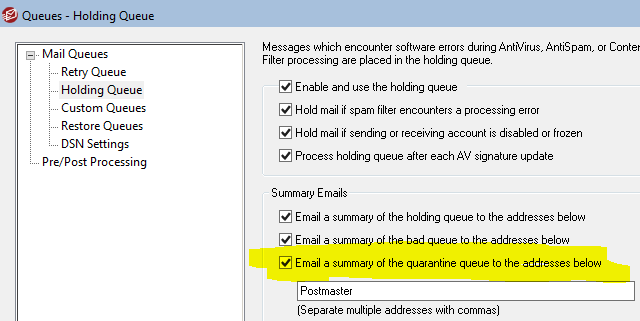
As shown above, when an email is found to be infected it moves it into the Quarantine Queue with an associated reason (the X-MDBadQueue-Reason header) so you’d also get alerted about it based on this option in Queues -> Mail Queues / DSN…
Files that cannot be scanned (eg. password protected files) are not quarantined and remain in the mailbox.
4) Block suspect office documents
You can also configure Clam Antivirus to block Office documents that contain Macro’s outright (these Fake Invoice documents seem to be using them if they are directly attached to the email rather than a link to them).
To do this open \MDaemon\SecurityPlus\ClamAVPlugin\conf\clamd.conf in a text editor and add the following then restart MDaemon to pick up the change…
#With this option enabled OLE2 files with VBA macros, which were not detected by #signatures will be marked as “Heuristics.OLE2.ContainsMacros”.
OLE2BlockMacros Yes
(Note: this entry doesn’t exist by default so you must add it rather than look to edit an existing entry)
5) Turn on ‘Refuse non-RFC compliant email’ (NEW)
In many of these cases, the Fake Invoice email that arrives contains multiple email addresses in the FROM header to make it look to the recipient that it’s from a valid sender you may have dealt with before.
The latest version of MDaemon (18.5.1) has enhanced the Setup -> Server Settings -> Servers -> Refuse Messages which violate RFC standards check and if this option is enabled (ON by default on new installations) it will now reject emails that have a FROM header content like this.
Other suggestions
Passwords
Ensure users have strong mailbox passwords that are unique to their mailbox to help ensure there is no risk of email spoofing.
A good website that helps identify accounts you might want to review the passwords for is https://haveibeenpwned.com/
Territory blocking
Use Security -> Security Settings -> Screening -> Location Screening to block geographic locations where nothing genuine would ever connect and send an email via an authenticated session. This way even if an account password becomes known the nature of the geographic location means the malicious attempt is still refused.