02 Sep What is an SPF (Sender Policy Framework) Record and Why Do You Need One?
 As with a lot of new technologies the real power comes from when they are used by the masses.
As with a lot of new technologies the real power comes from when they are used by the masses.
Sender Policy Framework or SPF is no longer a new technology and is generally widely used to help preserve email domain reputation for large organisations, but it’s as well-known about in the Small to Medium sized business end of the email market.
Spammers know this and have started to target domains that do not have valid SPF records as they can most easily be used to spoof and send spam claiming to be from valid companies. Often these types of spoofed email are used in phishing attacks to then harvest more valuable data, so the smaller companies that can adopt the use of SPF the better.
In this guide, I hope to explain in a simple way what SPF does, how it can be configured, and what real world considerations need to be made to ensure it does not do more harm that good.
Protecting your domain identity with SPF
The name Sender Policy Framework does give a clue to what SPF is all about. Its main role is to define a policy that controls who, or more specifically which servers are allowed to send email claiming to be from your domain. Without SPF any email that is sent using your domain has to be considered to be possibly valid, regardless of what server is sending it and this leads to large amounts of spoof email. Very bad news for large corporate organisations, but now a major concern for even the smallest companies that use their own email domain.
By creating a Public SPF DNS record we can publicly announce which Internet servers are allowed to send email for our own specific domain.
Lets look at this from a diagrammatic point of view..
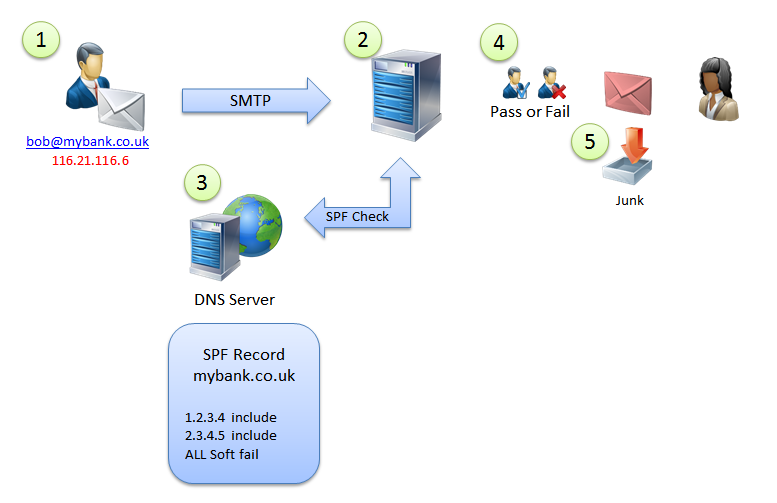
1. Sender claiming to be bob@mybank.co.uk opens an SMTP session to your mail server.
2. Before your mail server accepts the session it requests the SPF record for ‘mybank.co.uk’ from the DNS server.
3. The DNS server locates the SPF record for mydomain.co.uk via the DNS cloud and returns all valid sending servers and also what to do if a match is not found.
4. Your mail server uses this information to decide the sender is not allowed and follows the rule to ‘Soft Fail’ this message. It is still accepted and you tag it as spam.
5. The mail server is configured to put soft failed email into the user’s junk email folder.
What does an SPF record look like and how is it created?
An SPF record is a line of text that lists the mail servers that pass or fail a request.
The DNS record is therefore of type ‘txt’ and will look similar to this…
example.com. IN TXT "v=spf1 ip4:192.0.2.0/24 ip4:198.51.100.123 a -all"
The section between the quotes is the actual policy.
Let’s break down the example above…
v=spf1 This is the header that shows this is an SPF record
ip4:192.0.2.0/24 This is allowing any IP address in the range 192.0.2.X
ip4:198.51.100.123 This is allowing the specific IP address 198.51.100.123
a This is allowing any valid ‘a’ records for the domain
-all This fails all other IP’s ( notice the minus symbol this is a Hard Fail)
So, in essence, the point of the SPF record is to list all allowed servers either by IP, name or alternatively you can simply use ‘mx’ to say all mx records for this domain. For example…
example.com. IN TXT "v=spf1 mx -all"
…would only pass the listed MX records of a domain and all other servers would fail.
For a full breakdown of the options in SPF records see http://en.wikipedia.org/wiki/Sender_Policy_Framework
Hard fail vs Soft fail
In the above example, we are issuing what is known as a Hard fail. This means that if the sending server is not on the allowed list then we want the receiving server to not accept the message at all. There is another option though. Instead, we can return a ‘Soft fail’. The receiving server would then usually accept the message but tag it as ‘suspicious’ and warn the recipient.
To return a soft fail we use the ‘~’ tild character rather that ‘-‘ Minus. For example…
example.com. IN TXT “v=spf1 ip4:192.0.2.0/24 ip4:198.51.100.123 a ~all”
Checking your own domain
If you think you have already configured an SPF record for your domain this can quickly be checked using the windows nslookup command.
For example to check for SPF records on the domain example.com you would type the following command…
nslookup -type=txt example.com
This should show all text ‘txt’ domain records for a domain including any SPF records in the format shown above.
Update: If you find decoding the TXT records a little difficult to visualise Dmarcian.com have an excellent online SPF visualisation tool that makes this much easier to understand
What Mail Servers should send valid email from your domain?
Deciding what mail servers should send valid email for your domain sounds simple enough and definitely should include any local on-premise servers like Exchange or MDaemon, but there may be more servers you need to add that you can often overlook. For example, if you use any external email marketing solutions like ‘Mail Chimp’ these will often need to send valid mail using your domain and so if not added would fail any SPF checks. These types of services are aware of this issue and should be able to tell you what servers need adding to pass checks.
Tip mail chimp defines their servers in a separate txt record and this can be included using the ‘include’ tag
e.g. “v=spf1 mx a include:servers.mcsv.net -all”
This adds all servers as defined in the servers.mcsv.net record, so you can chain SPF records together for easier management and to get around problems with updating multiple records.
How do you setup an SPF record
As SPF records are DNS records the exact procedure does depend on the tools that your DNS provider provide to add and maintain domain records.
From a technical point of view, you need to create a domain ‘txt’ record on the root of your domain records, and the txt is a simple string as in the examples. Often you can edit records via a web interface and this should allow you to experiment, don’t forget you can always test the records using the ‘nslookup’ command as I have shown above.
If your DNS provider does not provide a web interface to allow you manage your records you may have to contact them directly and request that an SPF record is created, but as this is a widely used technology they should have experience of doing this before.
For a more in-depth look at SPF records why not try out the excellent SPF checking site, SPFWizard www.spfwizard.net


